Polaris
Member
Staff member
3
YEARS
3 YEARS OF SERVICE
Shellcode reflective DLL injection (sRDI) is a technique that allows converting a given DLL into a position independent shellcode that can then be injected using your favourite shellcode injection and execution technique. In this lab I wanted to try this technique as I think it is an amazing technique to have in your arsenal.
Execution
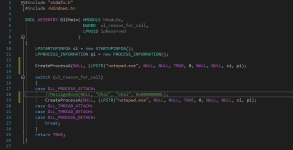
Let's compile a simple x86 DLL - in my case, an odd DLL that pops 2 notepad processes when executed:
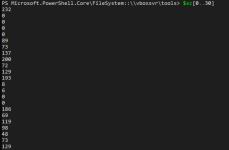
Convert the DLL into shellcode. We will get an array of shellcode bytes represented in decimal values:
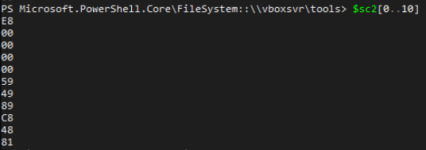
Let's convert them to hex:
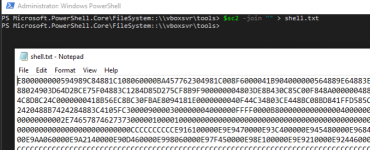
Join them all and print to a text file:
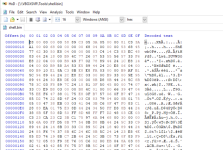
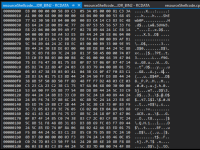
Create a new binary file with the shellcode we got earlier - just copy the hex string (as seen in the above screenshot) and paste it to a new file using HxD hex editor:
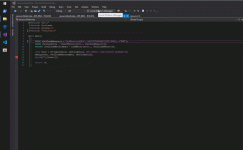
In order to load and execute the shellcode, we will place it in the binary as a resource as described in my other lab
Compile and run the binary. If the shellcode runs successfully, we should see two notepad.exe processes popup:
Execution
Let's compile a simple x86 DLL - in my case, an odd DLL that pops 2 notepad processes when executed:

Convert the DLL into shellcode. We will get an array of shellcode bytes represented in decimal values:
Code:
$sc = ConvertTo-Shellcode \\VBOXSVR\Experiments\messagebox\messagebox\Debug\messagebox.dll
Let's convert them to hex:
Code:
$sc2 = $sc | % { write-output ([System.String]::Format('{0:X2}', $_)) }
Join them all and print to a text file:
Code:
Join them all and print to a text file:
Create a new binary file with the shellcode we got earlier - just copy the hex string (as seen in the above screenshot) and paste it to a new file using HxD hex editor:

In order to load and execute the shellcode, we will place it in the binary as a resource as described in my other lab

Compile and run the binary. If the shellcode runs successfully, we should see two notepad.exe processes popup:
